Updating wordlists from Elasticsearch
Among the many benefits of running a honeypot is gathering the credentials intruders try in order to log in. As explained in some earlier blog posts, my Cowrie honeypots are redirecting secondary connections to another honeypot running INetSim. For example, an intruder logged in to a Cowrie honeypot may use the established foothold to make further attempts towards other services. INetSim regularly logs various attempts to create fake Facebook profiles, log in to various mail accounts, and submit product reviews.

Top 15 hostnames that honeypot intruders try to submit data to
INetSim activity is obviously tracked as well, which means that login credentials used by Cowrie intruders to gain further access elsewhere will also be stored. I’m logging all honeypot activity to Elasticsearch for easy analysis and for making nice visualizations.
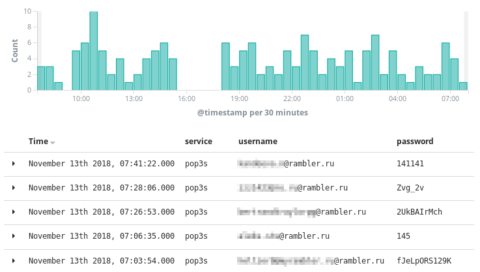
Most recent usernames and passwords used by intruders
Real passwords are always nice to have for populating wordlists used for e.g. password quality assurance, as dictionary attacks are often more efficient than bruteforcing. For this purpose I’m maintaining a local password list extracted from Elasticsearch. With the recent addition of the SQL interface, this extraction process was easy to script.
#!/bin/bash
PASSFILE=/some/path/to/honeypot_passwords.list
TODAY=$(date +%Y.%m.%d)
echo "select \"cowrie.password\" from \"logstash-${TODAY}\" \
where \"cowrie.password\" is not null;" \
| /usr/share/elasticsearch/bin/elasticsearch-sql-cli 2>&1 \
| tail -n +7 | head -n -1 | sort -u \
| sed -e 's/^[[:space:]]*//' -e 's/[[:space:]]*$//' \
| while read p; do
grep -qax "${p}" ${PASSFILE} || echo "$p" | tee -a ${PASSFILE}
done
echo "select \"password\" from \"logstash-${TODAY}\" \
WHERE \"service\" IS NOT NULL AND \"password\" IS NOT NULL\
AND MATCH(tags, 'inetsim');" \
| /usr/share/elasticsearch/bin/elasticsearch-sql-cli 2>&1 \
| tail -n +7 | head -n -1 | sort -u \
| sed -e 's/^[[:space:]]*//' -e 's/[[:space:]]*$//' \
| while read p; do
grep -qax "${p}" ${PASSFILE} || echo "$p" | tee -a ${PASSFILE}
done
This script (although with some more pipes and filters) is regularly run by cron, continuously adding more fresh passwords to the local wordlist.