Perfectly synchronized dual portscanning
The other day while reviewing my fireplot graphs, I noticed (yet) another portscan. They’re not unusual. This one took around four and a half hour to complete, and covered a lot of TCP ports on one IPv4 address. That’s not unusual either. The curved graph shown below is caused by the plot’s logarithmic Y axis, where approximately linear activity will be presented as a curve. The scanning speed changed above TCP port 10000, when the scanner started increasing the interval between ports hence the “elbow” in the graph. Such behaviour is seen less often.
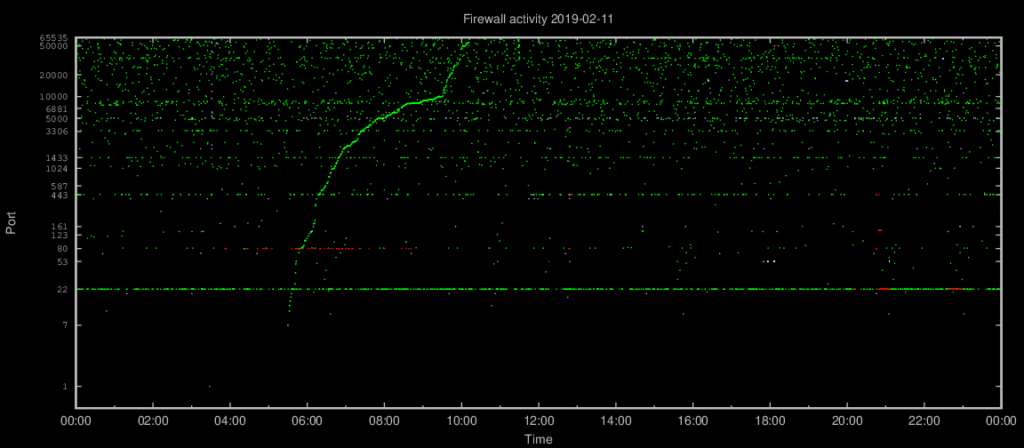
Port scans in general are mostly harmless and not worth pursuing, but I often check the source IP address anyway. What caught my attention this time was that each TCP port probe was performed from the same two IP addresses at the exact same time.

Now and again, more than one source IP address inevitably hits the same destination address at the same time. In this case, however, the two source IP addresses, from Verizon and China Telecom respectively, probed each and every destination port in the port scan simultaneously. The second source IP address usually did one additional probe after about a second before they both moved on to the next port. Here’s a short log extract:
06:18:02 - 205.205.150.21:60298 -> my.ip:444
06:18:02 - 14.135.120.21:61829 -> my.ip:444
06:18:03 - 14.135.120.21:61829 -> my.ip:444
06:19:25 - 205.205.150.21:52087 -> my.ip:445
06:19:25 - 14.135.120.21:58357 -> my.ip:445
06:19:26 - 14.135.120.21:58357 -> my.ip:445
06:19:55 - 205.205.150.21:51165 -> my.ip:465
06:19:55 - 14.135.120.21:49536 -> my.ip:465
06:19:55 - 14.135.120.21:49536 -> my.ip:465
06:21:42 - 205.205.150.21:51622 -> my.ip:502
06:21:42 - 14.135.120.21:60555 -> my.ip:502
06:21:43 - 14.135.120.21:60555 -> my.ip:502
06:22:15 - 205.205.150.21:59264 -> my.ip:503
06:22:15 - 14.135.120.21:58707 -> my.ip:503
06:22:16 - 14.135.120.21:58707 -> my.ip:503
06:23:17 - 205.205.150.21:63830 -> my.ip:515
06:23:17 - 14.135.120.21:65380 -> my.ip:515
06:23:18 - 14.135.120.21:65380 -> my.ip:515
06:25:00 - 205.205.150.21:57614 -> my.ip:523
06:25:00 - 14.135.120.21:65188 -> my.ip:523
06:25:01 - 14.135.120.21:65188 -> my.ip:523
06:26:34 - 205.205.150.21:50725 -> my.ip:548
06:26:34 - 14.135.120.21:60536 -> my.ip:548
06:26:35 - 14.135.120.21:60536 -> my.ip:548
06:27:27 - 205.205.150.21:52714 -> my.ip:554
06:27:27 - 14.135.120.21:53459 -> my.ip:554
06:27:27 - 14.135.120.21:53459 -> my.ip:554
06:28:09 - 205.205.150.21:59443 -> my.ip:587
06:28:09 - 14.135.120.21:64735 -> my.ip:587
06:28:10 - 14.135.120.21:64735 -> my.ip:587
06:30:25 - 205.205.150.21:57621 -> my.ip:631
06:30:25 - 14.135.120.21:51887 -> my.ip:631
06:30:26 - 14.135.120.21:51887 -> my.ip:631
06:31:20 - 205.205.150.21:53968 -> my.ip:636
06:31:20 - 14.135.120.21:61462 -> my.ip:636
06:32:04 - 205.205.150.21:64024 -> my.ip:666
06:32:04 - 14.135.120.21:57281 -> my.ip:666
06:32:05 - 14.135.120.21:57281 -> my.ip:666
06:33:15 - 205.205.150.21:55499 -> my.ip:774
06:33:15 - 14.135.120.21:63834 -> my.ip:774
06:33:16 - 14.135.120.21:63834 -> my.ip:774
06:34:31 - 205.205.150.21:58959 -> my.ip:789
06:34:31 - 14.135.120.21:49894 -> my.ip:789
06:34:32 - 14.135.120.21:49894 -> my.ip:789
06:36:05 - 205.205.150.21:54622 -> my.ip:873
06:36:05 - 14.135.120.21:53988 -> my.ip:873
06:36:05 - 14.135.120.21:53988 -> my.ip:873
06:36:52 - 205.205.150.21:49230 -> my.ip:902
06:36:52 - 14.135.120.21:49321 -> my.ip:902
06:36:52 - 14.135.120.21:49321 -> my.ip:902
As the log shows, the two source IP addresses, most likely unknowingly parts of a botnet, were working in perfect synchronization. The timing is too precise to be two individual scanning processes on opposite sides of the globe just started and left to run, so this scan was likely to have been under external control.